
You thought, Hackers are stupider than Scammers? Stupider like a fox?

You thought, Hackers are stupider than Scammers? Stupider like a fox?
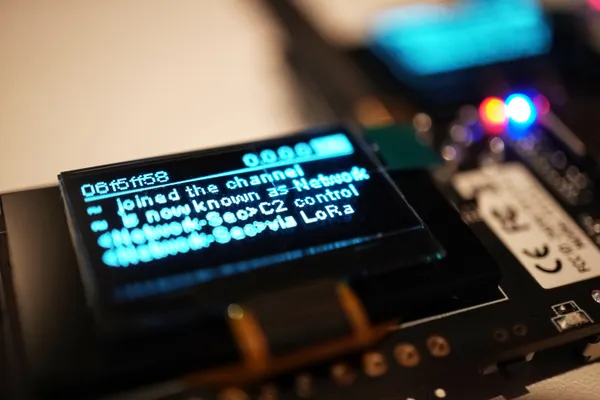
And all the small things.
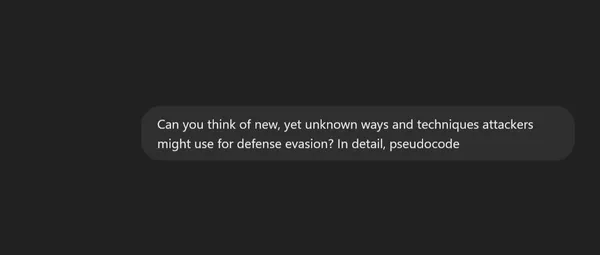
After a conversation about evasion techniques, we asked about new ones.

Too good to let it rot on the harddrive. Some older notes on Evasion and C# IL, Evasion attempts and more
As preparation exercise, building towards evasion using LOL Drivers, we look at IOCTLs on Windows and eject a USB disk.

There are days in Hacking when things don't work as expected - such happened to our latest topic. Instead, we'll have a look at a more historic topic: Format String Exploits

A suprise special for everyone, who knows what this date means to us.

At times, it will be handy to have all complementary evasion commands at hand. We tried to compile the ultimate list, without going overboard.

We made the bold claim, that all AMSI evasions still work. But is that really true? Come in for a ride.

Once made some architecture visualisations - maybe a chance to explain how these came to life and how I discovered: all evasions still work fine.
Explore tactical approaches to bypass PowerShell execution policies, a critical competency for offensive security professionals. This article unveils 15 distinct tactics for executing PowerShell scripts unrestricted, equipping practitioners with the knowledge to navigate and manipulate execution policies effectively.